
You’ve completed your annual phishing training. This includes teaching employees how to spot phishing emails. You’re feeling good about it. That is until about 5-6 months later. Your company suffers […]
Read more ›
The number of internet-connected devices in homes has been growing. It’s increased exponentially over the last decade. A typical home now has 10.37 devices connected to the internet. PCs and […]
Read more ›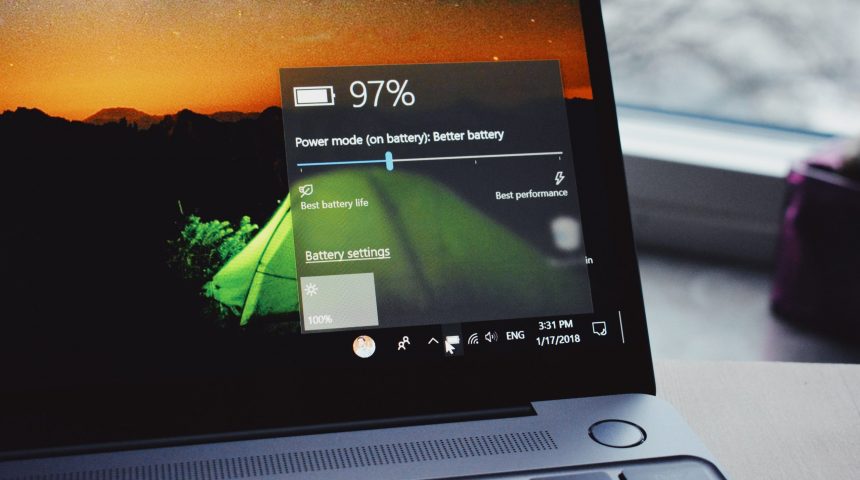
One of the big draws of a laptop computer is that you can use it anywhere. You don’t need to have it plugged in all the time because it has […]
Read more ›
“Hybrid office” is the new buzzword you’ll hear used in business discussions. It’s the mix of having employees both working at the office and working from home. This has become […]
Read more ›
Credential theft is now at an all-time high and is responsible for more data breaches than any other type of attack. With data and business processes now largely cloud-based, a […]
Read more ›
Smartphones and tablets are often the preferred device for communications, web searching, and accessing many types of apps. They’re more portable and can be used from anywhere. We’re seeing the […]
Read more ›
Approximately 34% of businesses take a week or longer to regain access to their data and systems once hit with a malware attack. Malware is an umbrella term that encompasses […]
Read more ›
One of the most important applications we choose is our internet browser. When on a computer or a mobile device, we work in that most of the time because many […]
Read more ›
While many companies have moved most of their workflows to the cloud, there is still a key component of office operations that is location-based. This would be employee computers. Most […]
Read more ›
When you see those people with two monitors, you may assume they do some specialized work that requires all that screen space, or they just really like technology. But having […]
Read more ›